What is “Open Source” or the layman’s guide to getting your software for nothing and saving “cloud” costs.
Lets get a grounding before we start, you don’t buy or own software, you are paying for a licence t o use it. Whether it comes in a smart box with a CD and activation code or you download it from the Internet, its never yours, you are just licencing it. The licence will tell you how you can use it, on what, how many and who and why. The normal model is that you pay an amount and then you can use that software in accordance with the terms and conditions usually called a EULA or End User Licence Agreement. In paying the fee you agree to the EULA.
o use it. Whether it comes in a smart box with a CD and activation code or you download it from the Internet, its never yours, you are just licencing it. The licence will tell you how you can use it, on what, how many and who and why. The normal model is that you pay an amount and then you can use that software in accordance with the terms and conditions usually called a EULA or End User Licence Agreement. In paying the fee you agree to the EULA.
There has been a push to make software licencing more and more expensive. This is to push small business to the cloud where they pay monthly and usually end up paying three times as much over a five year period compared to having the software working in-house. The big companies such as Microsoft and Sage think you don’t have an alternative.
There are alternatives to Sage, Microsoft SQL, Exchange, ACT! etc, and that is to use open source software in house on your own hardware. Its what Unilever, Tesco, Amazon, Google and many more do, so read on. or go to https://www.youtube.com/watch?v=a8fHgx9mE5U To see it explained using Lego.
“free” as in freedom, not free as in beer.
Some companies don’t charge for the software licence, a famous one for this is AVG and their model is that some people will go on to purchase a licence, so they give it away as a temptation or loss-leader.
There is another category, the Open Source licence. There are many variations but essentially they will grant you a licence to use, modify and distribute the software at zero cost. Basically you obtain it for nothing and you are own your own. You install it, you configure it and you solve any problems. Well that’s fine if you are an IT company but what if you aren’t and you want to use the software but don’t have a server or anyone to help?
The answer is simple, you pay someone to do it for you. They will charge you a monthly amount to load the software on their servers, give you access and help you use it. So Open Source doesn’t mean free in this case. This means you are free to use it and change it but it may cost you money. We prefer the term free licence.
How to save 82% on your software costs
The difference is quite simple. Lets say you want an e-mail server. You can buy a server and load Microsoft Server and Exchange software on it. This will cost you the software at around £5,000 including licences for ten users. Every user you add will cost you more. The charge for installing that would be around £300 and you will pay monthly for support from the supplier of around £500 a year. That’s a total cost of ownership (TCO) of £7,800 for five years use. I am ignoring hardware costs.
If you decide that you want to use e-mail but on the Internet with the same facilities the you will pay £3,000 but it might not be Microsoft, it might be Zimbra, which works the same, does the same but its open source. You are paying the people at Zimbra to do it all for you.
If you decide to install Zimbra on your own server then this is where we come in. You pay the same for the installation and support as the first example but the licensing cost is zero, so the TCO is now £1,425 because the large lump that went to Microsoft has disappeared.
You are happier as you pay less and get the same results and your supplier is happier because they take all of the £1,425 rather than a tiny part of £7,800. You have got the same result but have spent only 18% of the Microsoft solution. The other bonus is the hardware costs are reduced as Zimbra needs less computing oomph than Microsoft Exchange does.
There are plenty of Open Source alternatives
We call these clear alternatives. Your needs may be simple such as writing a letter and preparing a cash flow. It doesn’t matter how you do it as long as you end up with a letter and a cash flow. You can use any of the programs below to achieve this:
Microsoft Office Home & Small business £229.00 TCO over 5 years £229
Microsoft Office 365 £10 a month TCO over 5 years £600
Ability Office £30 TCO over 5 years £30
OpenOffice and Libre office £0 TCO over 5 years £0
The results are the same but Ability is just like using Microsoft but OpenOffice and Libre Office have their own menus.
But this stuff’s worthless!
A lot of people say that “anything free is worth what you pay for it”. A lot more say that other Office suites are no use or don’t work. So here are the simple facts; For most people this software will meet all of their needs.
Nobody uses this stuff!
For software that “nobody in their right mind would use” open source is doing very well indeed. 70% of all web servers are run using the Open Source Apache web server. Millions of web sites use the open source PHP web scripting languages. The Linux operating system, Mozilla Firefox, PERL (Web scripting language) and PNG (graphics file format) are all examples of very popular software that is based on open source.
A report by the Standish Group (from 2008) states that adoption of open-source software models has resulted in savings of about $60 billion per year to consumers. Open source has some very impressive backers. IBM – whose software department is bigger than Microsoft – fully endorses the Linux operating system (open source). Other large companies such as HP and Novell are backers as well. Each of these companies invest billions in this technology.
The term “open source” software is used by some people to mean more or less the same category as free software. It is not exactly the same class of software: they accept some licenses that we consider too restrictive, and there are free software licenses they have not accepted. However, the differences in extension of the category are small: nearly all free software is open source, and nearly all open source software is zero cost.
Why zero cost?
If you want to establish yourself in the market place then give your licences away, people will take the software, modify it, improve it and find out the problems, at no cost to you. You can then implement the changes on your paid-for versions at a fraction of what it would have cost. In our earlier example there are 500,000,000 people using Zimbra.
So why isn’t it more plentiful?
Most computer installers are self trained or certified by Microsoft, so they have a one size fits all mentality. Big business uses Microsoft but more of them such as Amazon & Google use a variation of a product called UNIX. This is an open source operating systems which was developed by academics. Over the years it has grown, most mobile phones use it instead of Windows, Routers and every Apple item uses it. It’s technical and you cant just get on and use it, unless someone makes it friendly as Apple has done, but in it’s native form which is best for servers, its as friendly as a rabid, cornered, rat.
Anyone can install Windows badly but only the technically proficient can install UNIX. A server is a server and most users don’t go near it or work on it, as long as it does the job of delivering mail and data they don’t really care. For a computer person to migrate from Windows to UNIX would take years, we have had discussions with IT companies in Suffolk and they don’t have the capability or the need to supply UNIX because they can keep selling Microsoft solutions. We do both Microsoft and UNIX so we have the choice based on Clients needs, but then we don’t have sales people and don’t ignore the needs of small business.
Clear Alternatives
There are many alternatives but we have focussed on the market leaders. All our UNIX servers come pre-installed. All you pay for is the implementation, usually £300 and a support charge of £225 annually per module. Here is a list of popular software products and the equivalent that is pre-installed on all the servers we supply.
File server Samba
Sage Front Accounting ERP
ACT! Sugar CRM
Microsoft SQL MySQL , PostGRES
Microsoft IIs server Apache
DropBox OwnCloud
Microsoft Exchange Zimbra, SoGo
Veritas backup PCBackup
Microsoft Project OpenProject
Microsoft Dynamics ERP OpenERP









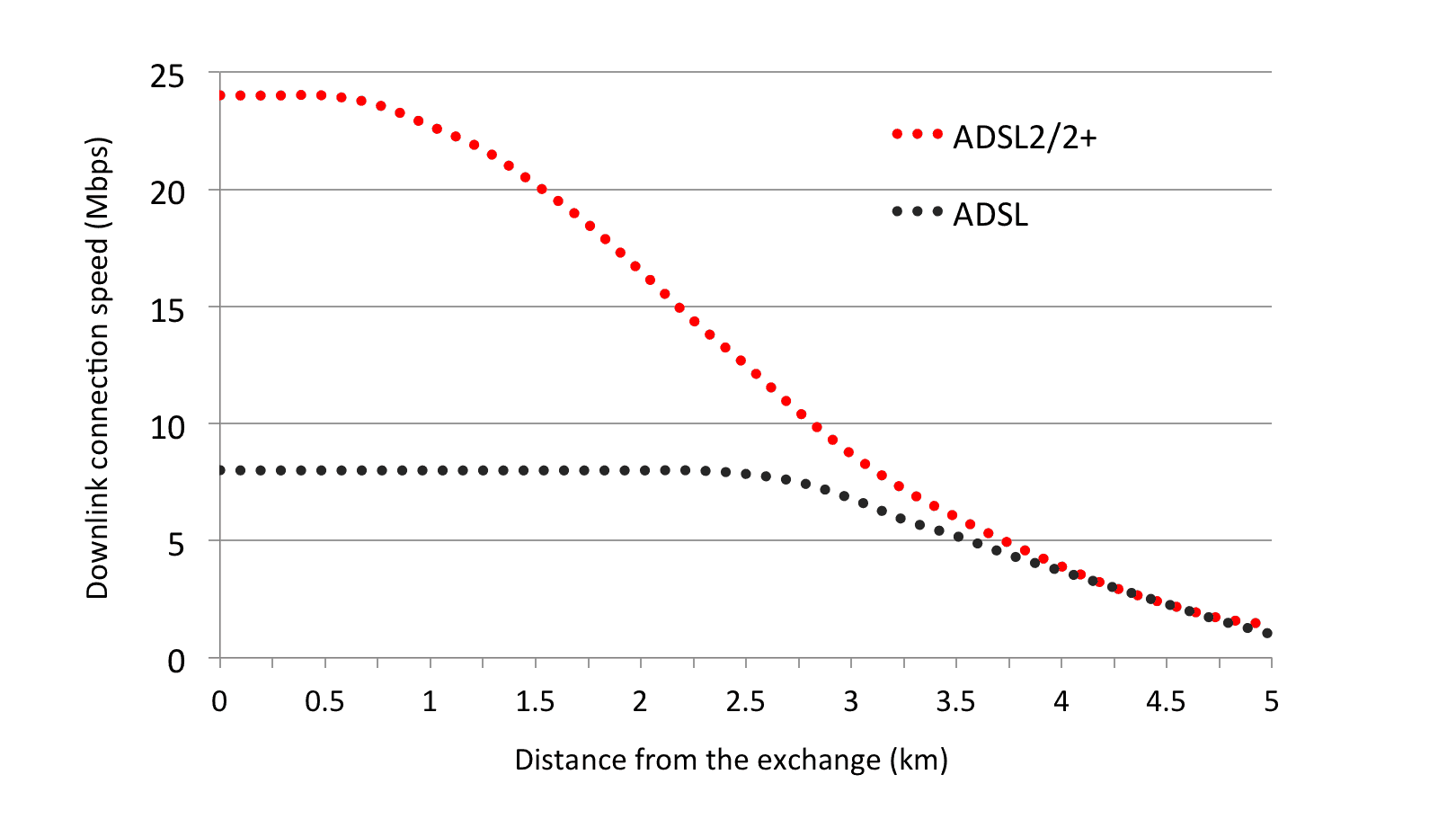 So if you leive near the exchange, which can anything from a large brick building with Openreach vans to a small brick building tucked away in larger villages You will get a good fast broodband signal. You can see how fast it tails off and at around 3km its getting bad. Remember it’s not how the bird flies but how far the cable travels. In the case we are quoting later the crow would fly 3 km but the cable snakes a 6.2km route to the property and through some pretty ropey cables and connectors.
So if you leive near the exchange, which can anything from a large brick building with Openreach vans to a small brick building tucked away in larger villages You will get a good fast broodband signal. You can see how fast it tails off and at around 3km its getting bad. Remember it’s not how the bird flies but how far the cable travels. In the case we are quoting later the crow would fly 3 km but the cable snakes a 6.2km route to the property and through some pretty ropey cables and connectors.
 “To be, or not to be: that is the question:
“To be, or not to be: that is the question:
 The size of the Space Shuttles booster rocket was decided by the size of a standard Roman horse’s backside. How come? Well read on and get to the end as there is a moral to this story.
The size of the Space Shuttles booster rocket was decided by the size of a standard Roman horse’s backside. How come? Well read on and get to the end as there is a moral to this story.